Request Quotas
Introduction
Request Quotas in Tyk Gateway allow you to set a maximum number of API requests for a specific API key or Policy over longer, defined periods (e.g., day, week, month). This feature is distinct from rate limiting (which controls requests per second), and it is essential for managing API consumption, enforcing service tiers, and protecting your backend services from sustained overuse over time.Key Benefits
- Enforce Usage Limits: Cap the total number of requests allowed over extended periods (days, weeks, months) per consumer.
- Implement Tiered Access: Easily define different usage allowances for various subscription plans (e.g., Free, Basic, Pro).
- Protect Backend Services: Prevent individual consumers from overwhelming upstream services with consistently high volume over long durations.
- Enable Usage-Based Monetization: Provide a clear mechanism for charging based on consumption tiers.
Quick Start
Overview
In this tutorial, we will configure Request Quotas on a Tyk Security Policy to limit the number of requests an API key can make over a defined period. Unlike rate limits (requests per second), quotas control overall volume. We’ll set a low quota limit with a short renewal period for easy testing, associate a key with the policy, observe blocked requests once the quota is exhausted, and verify that the quota resets after the period elapses. This guide primarily uses the Tyk Dashboard for configuration.Prerequisites
- Working Tyk Environment: You need access to a running Tyk instance that includes both the Tyk Gateway and Tyk Dashboard components. For setup instructions using Docker, please refer to the Tyk Quick Start.
- Curl, Seq and Sleep: These tools will be used for testing.
Instructions
Create an API
-
Create an API:
- Log in to your Tyk Dashboard.
- Navigate to API Management > APIs
- Click Add New API
- Click Import
- Select Import Type as Tyk API
- Copy the below Tyk OAS definition in the text box and click Import API to create an API.
Configure Policy and Quota
2. Create and Configure a Security Policy with a Request Quota: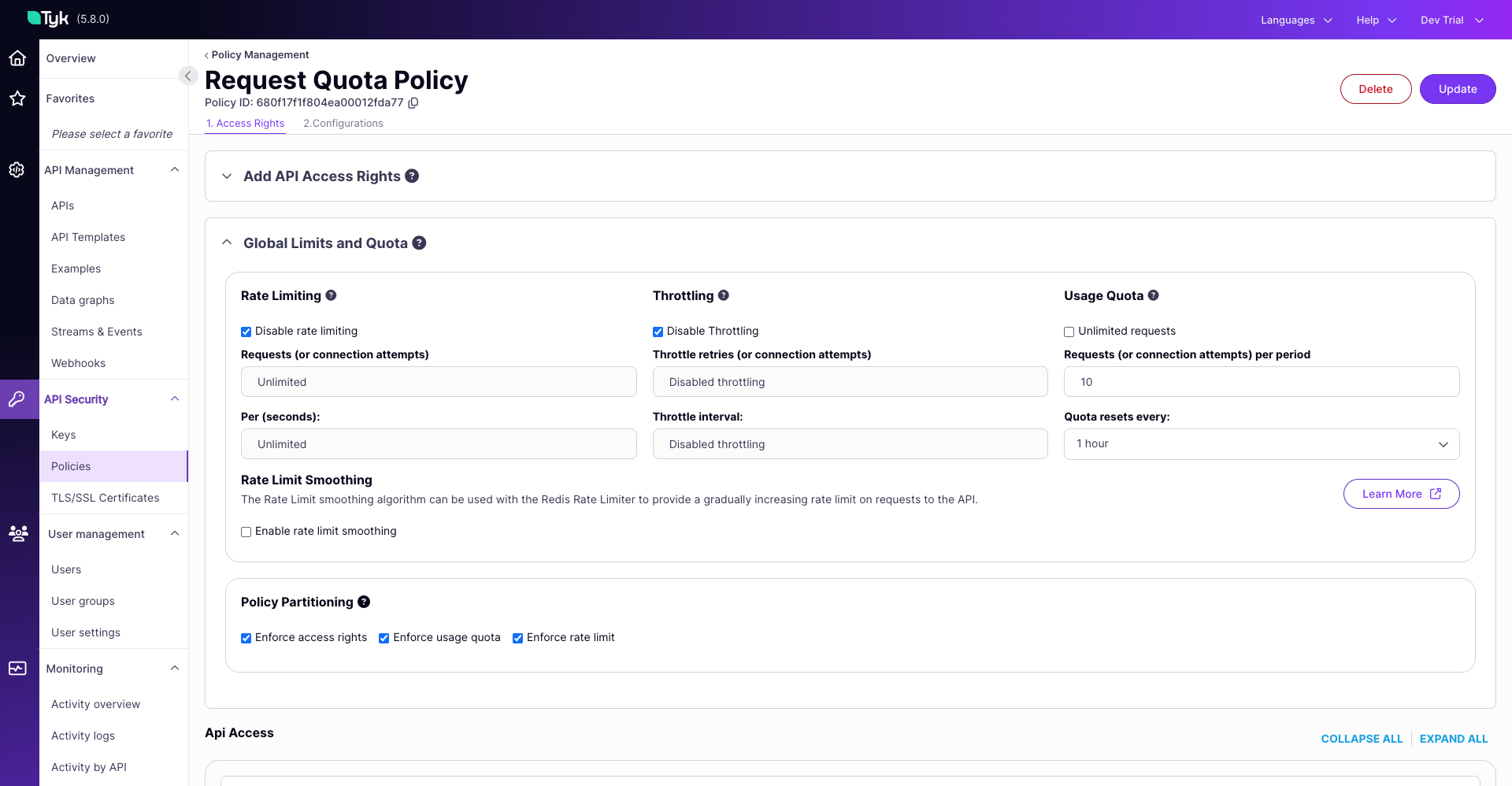
-
Update Quota Reset Period via API:
As the Dashboard UI doesn’t allow setting a shorter duration, we will set the Quota reset period to a value of 1 minute for testing purposes. The following commands search for the policy, modify its
quota_renewal_rateto 60 seconds, and update the API. Note: Obtain your Dashboard API key by clicking on the User profile at the top right corner, then click onEdit Profile, and select the key available underTyk Dashboard API Access Credentials. Now in the below command replace<your-api-key>with the API key you obtained from the Dashboard UI. - Associate an Access Key with the Policy:
Testing
-
Test Quota Exhaustion:
We’ve set a quota of 10 requests per 60 seconds. Let’s send more than 10 requests within that window to observe the quota being enforced.
- Open your terminal.
- Execute the following command, replacing
<replace-with-key-id>with the API Key ID you saved earlier. This command attempts to send 15 requests sequentially.
(Note: Thesleep 0.1adds a tiny delay, but ensure all 15 requests execute well within the 60-second quota window).- Expected Observation: You should see the first 10 requests succeed, returning an HTTP status code
200. After the 10th request, the subsequent requests (11 through 15) should be blocked by the quota limit, returning an HTTP status code403(Forbidden).
-
Test Quota Reset:
Now, let’s wait for the quota period (60 seconds) to elapse and then send another request to verify that the quota allowance has been reset.
-
Wait slightly longer than the reset period in the same terminal. The command below waits for 70 seconds.
-
Send one more request using the same API key:
-
Expected Observation: This request should now succeed, returning an HTTP status code
200. This demonstrates that because the 60-second quota period ended, the next request made after that period triggered the quota reset, replenishing the allowance.
-
Wait slightly longer than the reset period in the same terminal. The command below waits for 70 seconds.
Configuration Options
Request Quotas in Tyk can be configured at various levels. The configuration involves setting two specific fields:-
QuotaMax: The maximum number of requests allowed during the quota period.
- Set to
-1for unlimited requests - Set to a positive integer (e.g.,
1000) to limit total requests
- Set to
-
QuotaRenewalRate: The time in seconds for which the quota applies.
- Example:
3600for the hourly quota (1 hour = 3600 seconds) - Example:
86400for the daily quota (24 hours = 86400 seconds) - Example:
2592000for the monthly quota (30 days = 2592000 seconds)
- Example:
System-Level Configuration
Global quota settings are configured in the Tyk Gateway configuration file (tyk.conf). These settings affect how quotas are enforced across the entire gateway.
enforce_org_quotas: When set totrue, enables organization-level quota enforcementmonitor.enable_trigger_monitors: Enables quota monitoring and webhook triggersmonitor.global_trigger_limit: Percentage of quota usage that triggers alerts (e.g., 80.0 means 80%)monitor.monitor_user_keys: Enables monitoring for individual API keysmonitor.monitor_org_keys: Enables monitoring for organization quotas
API-Level Configuration
You cannot set quota values within an API Definition, but you can disable quota checking entirely for all requests proxied through that specific API, regardless of Key or Policy settings. This is useful if an API should never have quota limits applied.- skipQuota: When set to true, disables quota enforcement for the API.
- skipQuotaReset: When set to true, prevents quota counters from being reset when creating or updating quotas.
Configure via UI
The Tyk Dashboard provides a straightforward interface to set request quota parameters on Security Policies and Access Keys.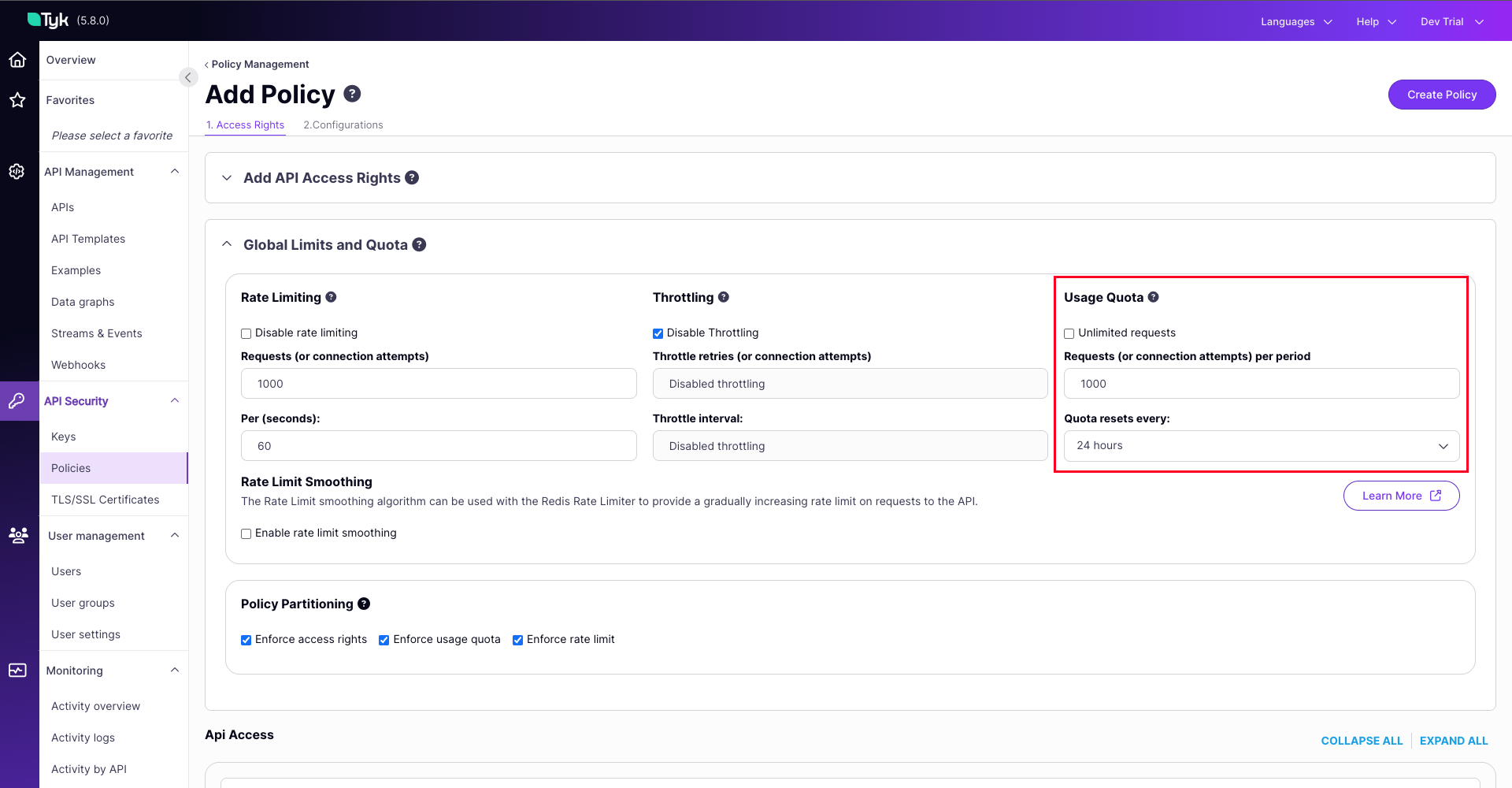
Configure via API
These are the fields that you can set directly in the Policy object or the Access Key:- Retrieve the policy object using
GET /api/portal/policies/{POLICY_ID} - Add or modify the
quota_maxandquota_renewal_ratefields within the policy JSON object - Update the policy using
PUT /api/portal/policies/{POLICY_ID}with the modified object, or create a new one usingPOST /api/portal/policies/
Important Considerations
- Policy Precedence: Quotas set on a Security Policy apply to all keys using that policy unless overridden by a specific quota set directly on the key (using the “Set per API Limits and Quota” option).
- Unlimited Quota: Setting
quota_maxto-1grants unlimited requests for the quota period. - Event-Driven Resets: Quotas reset after the
quota_renewal_rate(in seconds) has passed and upon the next request using the key. They do not reset automatically on a fixed schedule (e.g., precisely at midnight or the 1st of the month) unless external automation updates the session object. - Response Headers: When quotas are active, Tyk typically adds
X-RateLimit-Limit,X-RateLimit-Remaining, andX-RateLimit-Resetheaders to responses, allowing clients to track their usage. (Note: Header names might be configurable).
How It Works
Request Quotas in Tyk limit a client’s total number of API requests within a defined period (hours, days, months). Unlike rate limits that control the frequency of requests over short intervals (like seconds or minutes) to prevent immediate system overload, Request Quotas control the total volume of requests allowed over much longer periods to manage overall consumption and align with service tiers. When clients reach their quota limit, further requests are rejected until the quota period renews. It helps API providers implement usage-based pricing tiers, prevent API abuse, control infrastructure costs, and ensure fair resource distribution among clients. Think of Request Quotas as a prepaid phone plan with a fixed number of minutes per month. When you sign up, you get allocated a specific number of call minutes (API requests) that you can use over the billing period. You can make calls (API requests) at any pace you want – all at once or spread throughout the month – but once you’ve used up your allocated minutes, you can’t make any more calls until the next billing cycle begins.How Tyk Implements Quotas
Tyk implements request quotas using a Redis-based counter mechanism with time-based expiration. Here’s a detailed breakdown of the implementation:Core Components
-
Redis Storage: Quotas are tracked in Redis using incrementing counters for each API key. The TTL is set to the quota renewal period, and the counter is reset to 0 on the next request after expiration.
Here is a sample Redis key for a Request Quota:
Where:
scopeis optional and represents an API-specific allowance scopekey_hashis the hashed API key (if hash keys are enabled)
-
Session State: Quota configuration is stored in the user’s
SessionState, which contains several quota-related fields:QuotaMax: Maximum number of requests allowed during the quota period.QuotaRemaining: Number of requests remaining for the current period. Note: This is a derived value, not the primary counter.QuotaRenews: Unix timestamp when the quota will reset.QuotaRenewalRate: Time in seconds for the quota period (e.g., 3600 for hourly quotas).
-
Middleware: The quota check is performed by the
RateLimitAndQuotaCheckmiddleware
Quota Enforcement
The core logic for checking and enforcing Request Quotas is executed within theRateLimitAndQuotaCheck middleware, which is a step in the request processing pipeline. Here’s a breakdown of this process:
-
Initiation: As a request enters the Tyk Gateway, it passes through configured middleware. The quota validation process begins when it hits the
RateLimitAndQuotaCheckmiddleware. -
Applicability Check: The middleware first determines if quota enforcement is relevant:
- It checks the API Definition to see if quotas are globally disabled. If so, the process stops here for quotas and the request proceeds.
- It identifies the API key for the request and retrieves its associated
SessionState.
-
Retrieve Limits: The middleware accesses the
SessionStateto get the specific quota parameters applicable to this key and potentially the specific API being accessed (if per-API quotas are configured):QuotaMax: The maximum number of requests allowed.QuotaRenewalRate: The duration (in seconds) of the quota period for setting the TTL in Redis.
-
Redis Interaction & Enforcement: This is the core enforcement step, interacting directly with Redis:
- Construct Key: Generates the unique Redis key for tracking this specific quota counter (e.g.,
quota-{scope}-{api-key-hash}). - Check Expiry/Existence: It checks Redis to see if the key exists and if its TTL is still valid.
- Handle Renewal (If Expired/Missing): If the key doesn’t exist or its TTL has passed, Tyk initiates the renewal logic described previously (attempting a distributed lock, setting the counter to 0, and applying the
QuotaRenewalRateas the new TTL). - Increment Counter: Tyk atomically increments the Redis counter value. This operation returns the new value of the counter after the increment.
- Compare Against Limit: The middleware compares this new counter value against the
QuotaMaxretrieved from the session state. - Decision:
- If
new_counter_value <= QuotaMax: The request is within the allowed quota. - If
new_counter_value > QuotaMax: This request has exceeded the quota limit.
- If
- Construct Key: Generates the unique Redis key for tracking this specific quota counter (e.g.,
-
Outcome:
- Quota OK: The middleware allows the request to proceed to the next stage in the processing pipeline (e.g., other middleware, upstream service).
- Quota Exceeded: The middleware halts further request processing down the standard pipeline. It prepares and returns an error response to the client, typically
HTTP 403 Forbiddenwith a “Quota exceeded” message.
-
Session State Update: Regardless of whether the request was allowed or blocked due to the quota, the middleware calls an internal function (like
updateSessionQuota) to update the in-memorySessionStateassociated with the API key. This update synchronizes theQuotaRemainingfield in the session with the latest calculated state based on the Redis counter and its expiry. It ensures that subsequent operations within the same request lifecycle (if any) or diagnostic information have access to the most recent quota status.
Quota Reset Mechanisms
The available allowance (QuotaRemaining) for an API key is replenished back to its maximum (QuotaMax) through several distinct mechanisms:
-
Event-Driven Renewal (Primary Mechanism):
- Condition: This occurs after the time duration specified by
QuotaRenewalRate(in seconds) has elapsed since the quota period began (i.e., since the last reset or key creation/update). In Redis, this corresponds to the Time-To-Live (TTL) expiring on the quota tracking key. - Trigger: The reset is not automatic based on a timer. It is triggered by the next API request made using that specific key after the
QuotaRenewalRateduration has passed (and the Redis TTL has expired). - Process: Upon detecting the expired TTL during that next request, Tyk resets the Redis counter (typically by setting it to 0 and immediately incrementing it to 1 for the current request) and applies a new TTL based on the
QuotaRenewalRate. This effectively makes the fullQuotaMaxavailable for the new period starting from that moment.
- Condition: This occurs after the time duration specified by
-
Manual Reset via API:
- Mechanism: You can force an immediate quota reset for a specific API key by calling an endpoint on the Tyk Gateway Admin API.
- Effect: This action directly deletes the corresponding quota tracking key in Redis. The next request using this API key will find no existing key, triggering the renewal logic (Step 1) as if the period had just expired, immediately granting the full
QuotaMaxand setting a new TTL. This provides an immediate, on-demand refresh of the quota allowance.
-
Key Creation or Update:
- Trigger: When a new API key is created or an existing key’s configuration is updated (e.g., via the Dashboard or the Gateway API), Tyk reapplies the quota settings based on the current policy or key-specific configuration.
- Process: This typically involves setting the
QuotaRemainingvalue toQuotaMaxin the key’s session data and ensuring the corresponding Redis key is created with the correct initial value (or implicitly reset) and its TTL set according to theQuotaRenewalRate. This ensures the key starts with a fresh quota allowance according to its defined limits. - Exception: This behavior can be suppressed if the API definition includes the
DontSetQuotasOnCreatefield (referred to asSkipQuotaResetin the OAS specification), which prevents automatic quota resets during key creation or updates.
Key Technical Aspects
-
Time-Based Reset: Unlike rate limiting, which uses sliding windows, quotas have a fixed renewal time determined by
QuotaRenewalRate(in seconds) - Atomic Operations: Redis pipelining is used to ensure atomic increment and expiration setting:
- Race Condition Handling: Distributed locks prevent multiple servers from simultaneously resetting quotas
- Quota Scope Support: The implementation supports both global quotas and API-specific quotas through the scoping mechanism
FAQs
What are Request Quotas in Tyk?
What are Request Quotas in Tyk?
How do Request Quotas differ from Rate Limits?
How do Request Quotas differ from Rate Limits?
- Rate Limits control the frequency of requests (e.g., 10 requests per second) to prevent traffic spikes and ensure consistent performance
- Request Quotas control the total volume of requests over a longer period (e.g., 10,000 requests per month) to manage overall API consumption and often align with business/pricing models
How are Request Quotas configured in Tyk?
How are Request Quotas configured in Tyk?
What are the key parameters for Request Quotas?
What are the key parameters for Request Quotas?
quota_max: Maximum number of requests allowed during the quota periodquota_remaining: Number of requests remaining for the current periodquota_renewal_rate: Time in seconds during which the quota is valid (e.g., 3600 for hourly quotas)quota_renews: Timestamp indicating when the quota will reset
Can I disable Request Quotas for specific APIs?
Can I disable Request Quotas for specific APIs?
disable_quota flag to true in the API definition. This config will bypass quota checking for all requests to that API, regardless of any quotas set at the key or policy level.Refer this documentation.What happens when a Request Quota is exceeded?
What happens when a Request Quota is exceeded?
- The request is rejected with a 403 Forbidden status code
- A “QuotaExceeded” event is triggered (which can be used for notifications or monitoring)
- The client must wait until the quota renewal period before making additional requests
- The quota violation is logged and can be monitored in the Tyk Dashboard
How are Request Quotas tracked and stored?
How are Request Quotas tracked and stored?
- Quota keys are prefixed with “quota-” followed by the key identifier
- For each request, Tyk increments a counter in Redis and checks if it exceeds the quota_max
- When a quota period expires, the counter is reset
- For distributed deployments, quota information is synchronized across all Tyk nodes
Can I set different quotas for different endpoints within the same API?
Can I set different quotas for different endpoints within the same API?
How do organization-level quotas work?
How do organization-level quotas work?
enforce_org_quotas), Tyk tracks the combined usage of all keys in the organization and rejects requests when the organization quota is exceeded, regardless of individual key quotas.Can I monitor quota usage and receive notifications before quotas are exceeded?
Can I monitor quota usage and receive notifications before quotas are exceeded?
- You can set up trigger monitors with percentage thresholds
- When usage reaches a threshold (e.g., 80% of quota), Tyk can trigger notifications
- These notifications can be sent via webhooks to external systems
- The monitoring configuration is set in the
monitorsection of your Tyk configuration
Why isn't my quota resetting automatically at midnight?
Why isn't my quota resetting automatically at midnight?
How can I manually reset a quota for a specific key?
How can I manually reset a quota for a specific key?
- Navigate to the “Keys” section
- Find and select the key you want to reset
- Click on “Reset Quota” button
Does Tyk count failed requests against my quota?
Does Tyk count failed requests against my quota?
Why are my quota counts inconsistent in a multi-gateway setup?
Why are my quota counts inconsistent in a multi-gateway setup?
- Redis replication lag: If you’re using separate Redis instances with replication, there may be delays in syncing quota information
- Network latency: In geographically distributed setups, network delays can cause temporary inconsistencies
- Configuration issues: Each gateway must be properly configured to use the same Redis database for quota storage
Why do I see "Quota disabled" error logs when I've intentionally disabled quotas?
Why do I see "Quota disabled" error logs when I've intentionally disabled quotas?
quota_max to -1 (to disable quotas) would generate an error log message: Quota disabled: quota max <= 0. This was a known issue that has been fixed in more recent versions.If you’re still seeing these logs, consider:- Upgrading to the latest version of Tyk
- Adjusting your log level to reduce noise
- Using the API definition’s
disable_quotaflag instead of settingquota_maxto -1
Can I set quotas to only count successful requests?
Can I set quotas to only count successful requests?
- Implement a custom middleware plugin that conditionally decrements the quota based on response codes
- Use the Tyk Pump to track successful vs. failed requests separately in your analytics platform and implement quota management at the application level
What happens if I change a quota mid-period?
What happens if I change a quota mid-period?
- For increasing the quota: The new maximum will apply, but the current remaining count stays the same
- For decreasing the quota: If the new quota is less than what’s already been used, further requests will be rejected
- For changing the renewal rate: The new renewal period will apply from the next renewal
Can I implement different quota plans for different users?
Can I implement different quota plans for different users?
- Policies: Create different policies with varying quota limits and assign them to keys based on subscription level
- Key-specific settings: Override policy quotas for individual keys when necessary
- Meta Data: Use key metadata to adjust quota behavior through middleware dynamically
- Multiple APIs: Create separate API definitions with different quota configurations for different service tiers
How do I troubleshoot quota issues?
How do I troubleshoot quota issues?
- Check Redis: Ensure Redis is functioning properly and examine the quota keys directly
- Review logs: Look for quota-related messages in the Tyk Gateway logs
- Verify configuration: Confirm that quota settings are correctly configured in policies and API definitions
- Test with the API: Use the Tyk Gateway API to check quota status for specific keys
- Monitor request headers: Examine the
X-Rate-Limit-Remainingheaders in API responses