Kubernetes Demo
The tyk-k8s-demo repository allows you to start up an entire Tyk Stack with all its dependencies as well as other tools that can integrate with Tyk. The repository will spin up everything in Kubernetes usinghelm and bash magic
to get you started.
Purpose
Minimize the amount of effort needed to start up the Tyk infrastructure and
show examples of how Tyk can be set up in k8s using different deployment
architectures as well as different integrations.
Prerequisites
Required Packages
You will need the following tools to be able to run this project.- Kubectl - CLI tool for controlling Kubernetes clusters
- Helm - Helps manage Kubernetes applications through Helm charts
- jq - CLI for working with JSON output and manipulating it
- git - CLI used to obtain the project from GitHub
- Terraform (only when using
--cloudflag)
License Requirements
- Tyk OSS: No license required as it is open-source.
- Licensed Products: Sign up here using the button below, and choose “Get in touch” to receive a guided evaluation of the Tyk Dashboard and your temporary license.
.env file using the example provided and update it with your licenses as follows:
LICENSE, MDCB_LICENSE, and PORTAL_LICENSE
inside the .env file.
Minikube
If you are deploying this demo on Minikube, you will need to enable the ingress addon. You can do so by running the following commands:Quick Start
Possible deployments
-
tyk-stack: A comprehensive Tyk Self Managed setup for a single region -
tyk-cp: Tyk control plane in a multi-region Tyk deployment -
tyk-dp: Data plane of hybrid gateways that connect to either Tyk Cloud or a Tyk Control Plane, facilitating scalable deployments -
tyk-gateway: Open Source Software (OSS) version of Tyk, self-managed and suitable for single-region deployments
Dependencies Options
Redis Optionsredis: Bitnami Redis deploymentredis-cluster: Bitnami Redis Cluster deploymentredis-sentinel: Bitnami Redis Sentinel deployment
mongo: Bitnami Mongo database deployment as a Tyk backendpostgres: Bitnami Postgres database deployment as a Tyk backend
- cert-manager: deploys cert-manager.
- datadog: deploys Datadog agent and starts up Tyk Pump to push analytics data from the Tyk platform to Datadog. It will also create a Datadog dashboard for you to view the analytics.
- elasticsearch: deploys
Elasticsearch and starts up Tyk pump to push analytics data from the Tyk platform to Elasticsearch.
- elasticsearch-kibana: deploys the Elasticsearch deployment as well as a Kibana deployment and creates a Kibana dashboard for you to view the analytics.
- Jaeger: deploys the Jaeger operator, a Jaeger instance, and the OpenTelemetry collector and configures the Tyk deployment to send telemetry data to Jaeger through the OpenTelemetry collector.
- k6: deploys a Grafana K6 Operator.
- k6-slo-traffic: deploys a k6 CRD to generate a load of traffic to seed analytics data.
- keycloak: deploys the Keycloak Operator and a Keycloak instance.
- keycloak-dcr: starts up a Keycloak Dynamic Client Registration example.
- keycloak-jwt: starts up a Keycloak JWT Authentication example with Tyk.
- keycloak-sso: starts up a Keycloak SSO example with the Tyk Dashboard.
- newrelic: deploys New Relic and starts up a Tyk Pump to push analytics data from the Tyk platform to New Relic.
- opa: enables Open Policy Agent to allow for Dashboard APIs governance.
- opensearch: deploys OpenSearch and starts up Tyk Pump to push analytics data from the Tyk platform to OpenSearch.
- operator: deploys the Tyk Operator and its dependency cert-manager.
- operator-federation: starts up Federation v1 API examples using the tyk-operator.
- operator-graphql: starts up GraphQL API examples using the tyk-operator.
- operator-httpbin: starts up an API examples using the tyk-operator.
- operator-jwt-hmac: starts up API examples using the tyk-operator to demonstrate JWT HMAC auth.
- operator-udg: starts up Universal Data Graph API examples using the tyk-operator.
- portal: deploys the Tyk Enterprise Developer Portal as well as its dependency PostgreSQL.
- prometheus: deploys Prometheus and starts up Tyk Pump to push analytics data from the Tyk platform to Prometheus.
- prometheus-grafana: deploys the Prometheus deployment as well as a Grafana deployment and creates a Grafana dashboard for you to view the analytics.
- vault: deploys Vault Operator and a Vault instance.
Bash Script Usage
Start Tyk deployment
Create and start up the deploymentsStop Tyk deployment
Shutdown deployment--cloud flag
and requires the respective cloud CLI to be installed and authorized on your system. You will also need to specify the
CLUSTER_LOCATION, CLUSTER_MACHINE_TYPE, CLUSTER_NODE_COUNT, and GCP_PROJECT (for GCP only) parameters in the .env file.
You can find examples of .env files here:
For more information about cloud CLIs:
- AWS:
- GCP:
- gcloud
GOOGLE_APPLICATION_CREDENTIALSenvironment variable per documentation from Google
- Azure:
Customization
This repository can also act as a guide to help you get set up with Tyk. If you just want to know how to set up a specific tool with Tyk, you can run the repository with the--dry-run and --verbose flags. This will output all the commands that
the repository will run to stand up any installation. This can help debug as well as figure out what
configuration options are required to set these tools up.
Furthermore, you can also add any Tyk environment variables to your .env file and those variables will be mapped to
their respective Tyk deployments.
Example:
Variables
The script has defaults for minimal settings in this env file, and it will give errors if something is missing. You can also add or change any Tyk environment variables in the.env file,
and they will be mapped to the respective extraEnvs section in the helm charts.
| Variable | Default | Comments |
|---|---|---|
| DASHBOARD_VERSION | v5.5 | Dashboard version |
| GATEWAY_VERSION | v5.5 | Gateway version |
| MDCB_VERSION | v2.7 | MDCB version |
| PUMP_VERSION | v1.11 | Pump version |
| PORTAL_VERSION | v1.10 | Portal version |
| TYK_HELM_CHART_PATH | tyk-helm | Path to charts, can be a local directory or a helm repo |
| TYK_USERNAME | default@example.com | Default password for all the services deployed |
| TYK_PASSWORD | topsecretpassword | Default password for all the services deployed |
| LICENSE | Dashboard license | |
| MDCB_LICENSE | MDCB license | |
| PORTAL_LICENSE | Portal license | |
| TYK_WORKER_CONNECTIONSTRING | MDCB URL for worker connection | |
| TYK_WORKER_ORGID | Org ID of dashboard user | |
| TYK_WORKER_AUTHTOKEN | Auth token of dashboard user | |
| TYK_WORKER_USESSL | true | Set to true when the MDCB is serving on a TLS connection |
| TYK_WORKER_SHARDING_ENABLED | false | Set to true to enable API Sharding |
| TYK_WORKER_SHARDING_TAGS | API Gateway segmentation tags | |
| TYK_WORKER_GW_PORT | 8081 | Set the gateway service port to use |
| TYK_WORKER_OPERATOR_CONNECTIONSTRING | Set the dashboard URL for the operator to be able to manage APIs and Policies | |
| DATADOG_APIKEY | Datadog API key | |
| DATADOG_APPKEY | Datadog Application key. This is used to create a dashboard and create a pipeline for the Tyk logs | |
| DATADOG_SITE | datadoghq.com | Datadog site. Change to datadoghq.eu if using the European site |
| GCP_PROJECT | The GCP project for terraform authentication on GCP | |
| CLUSTER_LOCATION | Cluster location that will be created on AKS, EKS, or GKE | |
| CLUSTER_MACHINE_TYPE | Machine type for the cluster that will be created on AKS, EKS, or GKE | |
| CLUSTER_NODE_COUNT | Number of nodes for the cluster that will be created on AKS, EKS, or GKE | |
| INGRESS_CLASSNAME | nginx | The ingress classname to be used to associate the k8s ingress objects with the ingress controller/load balancer |
Docker Demo
Purpose
With tyk-demo repository, using docker-compose, you can set up quickly a complete Tyk stack, including dependencies and integrations. Minimize the amount of effort needed to start up the Tyk infrastructure and show end-to-end complete examples of how to set up various capabilities in Tyk as well as different integrations.Key Features
- Full Tyk stack deployment
- Pre-configured demo APIs
- Analytics and monitoring tools
- Integration with common third-party services
Prerequisites
- Docker compose Make sure you have docker compose and that docker is running on your machine.
- License key This Demo deploys and runs the full Tyk platform which is a licensed product. Please sign up using the button below, to obtain a license key. In the link, choose “Get in touch” to get a guided evaluation of the Tyk Dashboard and receive your temporary license.
Quick Start
The following steps will enable you to quickly get started:- Clone the repository:
- Navigate to the directory:
- Add license key to .env file:
- Run the setup script:
- Access Tyk Dashboard: http://localhost:3000
- Downloading and starting tyk-demo
- Setting up your license
- Logging in to Tyk Dashboard
Docker Compose Setup
Who is this page for?
This is the guide we recommend for a easy quick start. The instructions are the ones shared with you when you register to a free trial. You can also use this guide for your PoC since it spins up a full Tyk Self Managed stack for you using our project Docker Pro Demo, however, if you are interested in learning Tyk, there’s an option for Tyk Demo which is a project that spins up full Tyk stack that includes a prepopulate API definitions of all kinds, with various middleware options and can also spin up supporting tools such as Prometheus, Keycloak (IDP) etc.What’s included?
The Tyk Pro Docker Demo is our Self-Managed solution, which includes our Gateway, Dashboard, and analytics processing pipeline. This demo will run Tyk Self-Managed on your machine, which contains 5 containers: Tyk Gateway, Tyk Dashboard, Tyk Pump, Redis and MongoDB. This demo is great for proof of concept and demo purposes, but if you want to test performance, you will need to move each component to a separate machine.This demo is NOT intended for production use or performance testing, since it uses docker compose and the configuration files are not specifically tuned for performance testing or high loads. Please visit the Planning for Production page to learn how to configure settings for optimal performance.
The Tyk Pro Docker demo does not provide access to the Developer Portal.
Prerequisites
- Our Tyk Pro Docker demo on GitHub
- A Tyk Pro trial license
Steps for Installation
- Clone the GitHub repo
- Edit your hosts file
- Add your developer license
.env file - cp .env.example .env. Then add your license string to TYK_DB_LICENSEKEY.
- Initialise the Docker containers
- Bootstrap the Tyk installation
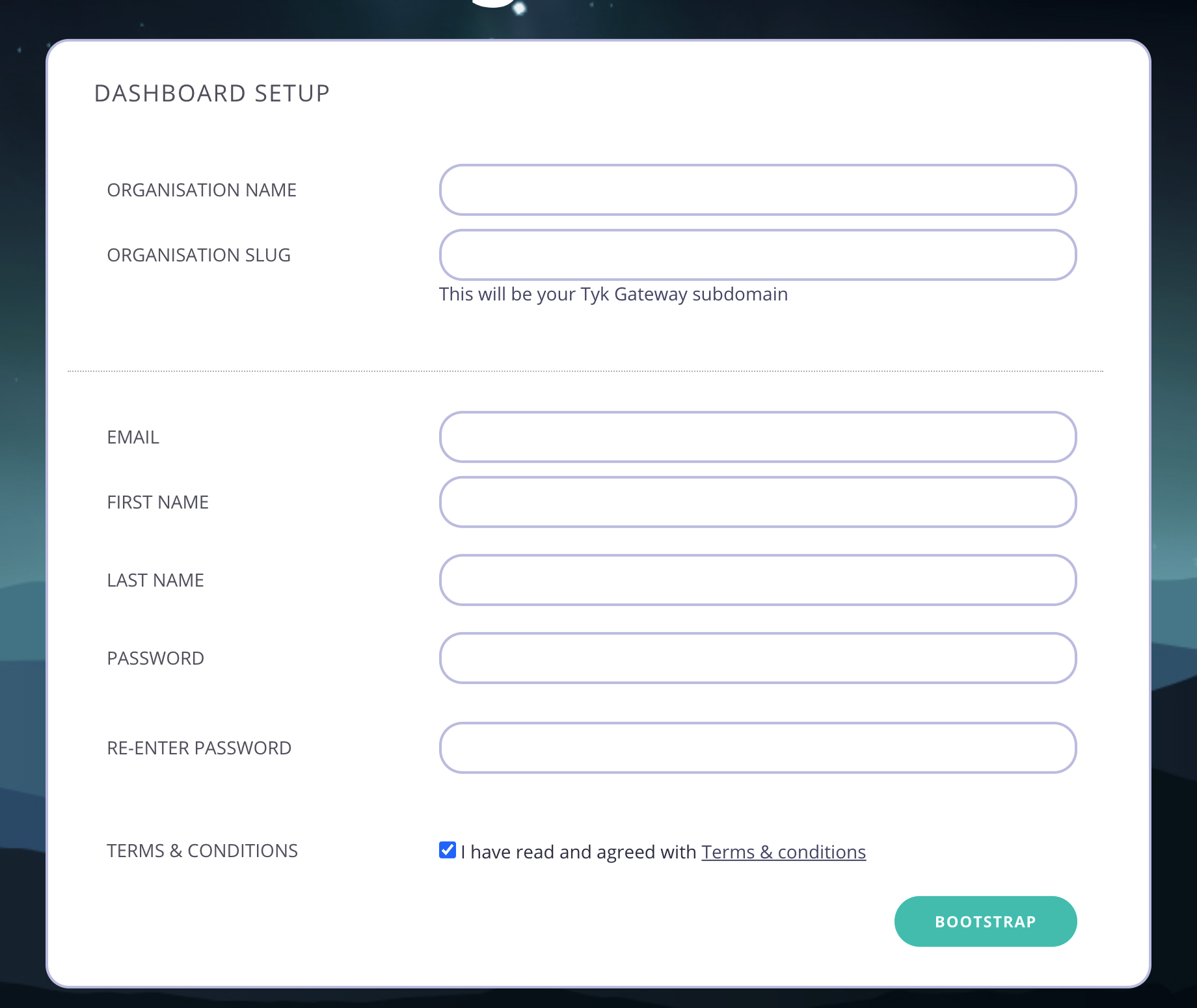
- Create your organization and default user
- Your Organization Name
- Your Organization Slug
- Your User Email Address
- Your User First and Last Name
- A Password for your User
-
Re-enter your user Password
For a password, we recommend a combination of alphanumeric characters, with both upper and lower case letters.
- log in to the Tyk Dashboard
127.0.0.1:3000, using the username and password created in the Dashboard
Setup screen.
Removing the demo installation
To delete all containers as well as remove all volumes from your host: With MongoDBUsing Windows
Tyk Pro on Windows using Docker Desktop
The Tyk Pro Docker demo is our full On-Premises Pro solution, which includes our Gateway, Dashboard, and analytics processing pipeline. This demo will run Tyk Self-Managed Pro on your machine, which contains 5 containers: Tyk Gateway, Tyk Dashboard, Tyk Pump, Redis and MongoDB. This demo is great for proof of concept and demo purposes, but if you want to test performance, you will need to move each component to a separate machine.This demo is NOT designed for production use or performance testing.
You use this at your own risk. Tyk is not supported on the Windows platform. However you can test it as a proof of concept using our Pro Demo Docker installation.
- MS Windows 10 Pro
- Docker Desktop for Windows running with a signed in Docker ID
- Git for Windows
- PowerShell running as administrator
- Postman for Windows
- Our Pro Demo Docker GitHub repo
- A free Tyk Self-Managed Developer license
\confs\tyk_analytics.conf file:
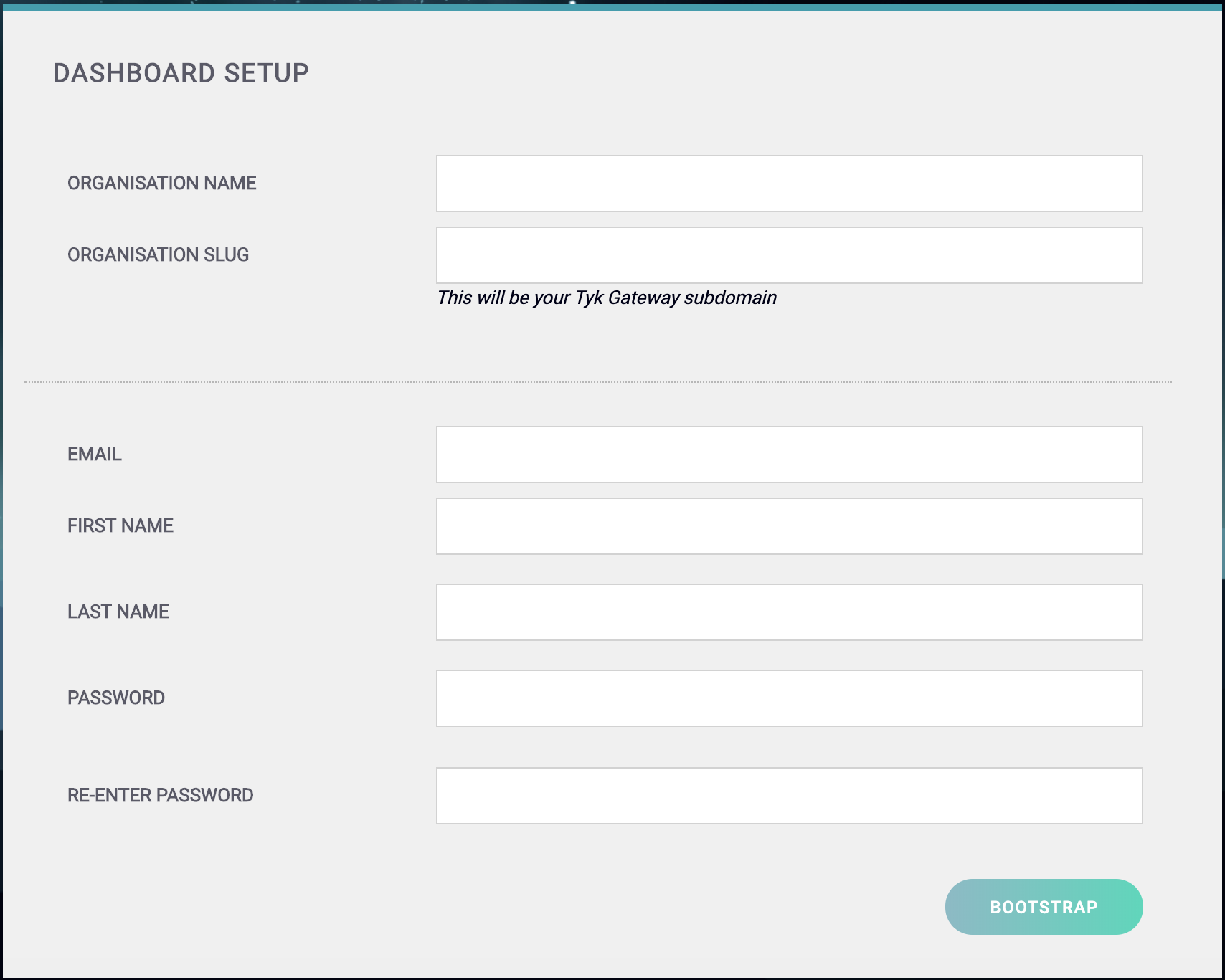
- Your Organization Name
- Your Organization Slug
- Your User Email Address
- Your User First and Last Name
- A Password for your User
-
Re-enter your user Password
For a password, we recommend a combination of alphanumeric characters, with both upper and lower case letters.
127.0.0.1:3000, using the username and password created in the Dashboard Setup screen.
Step 7 - Set up a Portal Catalog
This creates a portal catalog for your developer portal. For the Authorization Header, the Value you need to enter is the access_key value from the create user request. In the body add the org_id value created in Step One.
- Request: POST
- URL:
127.0.0.1:3000/api/portal/catalogue - Header: Key
AuthorzationValueSECRET_VALUE - Body (raw set to application/json):
Authorization Header, the Value you need to enter is the access_key value from the create user request.
- Request: POST
- URL:
127.0.0.1:3000/api/portal/catalogue - Header: Key
AuthorzationValueSECRET_VALUE - Body (raw set to application/json):
Authorization Header, the Value you need to enter is the secret value from your /confs/tyk_analytics.conf.
- Request: POST
- URL:
127.0.0.1:3000/api/portal/configuration - Header: Key
AuthorzationValueSECRET_VALUE - Body (raw set to application/json):
Tyk Pro on Windows using WSL
The Tyk Pro Docker demo is our full Self-Managed solution, which includes our Gateway, Dashboard, and analytics processing pipeline. This demo will run Tyk Self-Managed on your machine, which contains 5 containers: Tyk Gateway, Tyk Dashboard, Tyk Pump, Redis and MongoDB. This demo is great for proof of concept and demo purposes, but if you want to test performance, you will need to move each component to a separate machine.This demo is NOT designed for production use or performance testing.
You use this at your own risk. Tyk is not supported on the Windows platform. However you can test it as a proof of concept using our Pro Demo Docker installation.
- MS Windows 10 Pro with Windows Linux Subsystem enabled
- Docker Desktop for Windows running with a signed in Docker ID
- Git for Windows
- PowerShell running as administrator
- Postman for Windows
- Our Pro Demo Docker GitHub repo
- A free Tyk Self-Managed Developer license
- Optional: Ubuntu on Windows
\confs\tyk_analytics.conf file:
docker-compose.yml file, and change configs paths from related to absolute, and from linux format to windows format, like this:

- Your Organization Name
- Your Organization Slug
- Your User Email Address
- Your User First and Last Name
- A Password for your User
-
Re-enter your user Password
For a password, we recommend a combination of alphanumeric characters, with both upper and lower case letters.
127.0.0.1:3000, using the username and password created in the Dashboard Setup screen.
Configure your Developer Portal
To set up your Developer Portal follow our Self-Managed tutorial on publishing an API to the Portal Catalog.