Note for Tyk Cloud UsersThis documentation is for users who run their self-managed agents. If you’re using Tyk Cloud, agents are automatically managed for your Tyk Dashboard, and you don’t need to worry about installation, access tokens, or configuration. You can use the “Agents” and “API Provider” pages in the Tyk Cloud dashboard to check connection health between the agents and Governance Hub.
Availability
- Version: Available since v0.2
Overview
Agent and API Provider Management enables you to deploy, configure, and monitor the Tyk Governance agents that discover and synchronize APIs from various providers.Understanding Agents and API Providers
Agents are lightweight services that act as secure bridges between your API providers and the Tyk Governance Hub. They:- Run in your environment (on-premises, cloud, or hybrid)
- Connect to one or more API providers to discover APIs
- Securely transmit API data to the Governance Hub
- Support high availability deployments
- Can be monitored through the “Agents” section in the UI
- Tyk Dashboard
- AWS API Gateway
- How many APIs are discovered from each provider
- The connection status of each provider
- The last synchronization time
- Provider-specific details
Key Benefits
- Centralized Agent Visibility: Monitor all agents from a single dashboard
- Scheduled Synchronization: Configure automatic API discovery at regular intervals
- High Availability Deployment: Deploy multiple agent replicas with automatic leader election
- Detailed Status Monitoring: Track agent health, connection status, and synchronization history
- Secure Communication: All agent-to-hub communication is encrypted and authenticated
Dependencies
- Requires Tyk Governance and agents v0.2 or higher
- Agents support Kubernetes-based high availability, which requires Kubernetes cluster access
Quick Start
In this tutorial, we’ll set up a new agent, configure it to connect to an API provider, and monitor its status.Prerequisites
- Access to Tyk Governance Hub
- Access to an API provider (Tyk Dashboard or AWS API Gateway)
- A server or container environment to run the agent
Step-by-Step
-
Create a New Agent
-
From the Agents page, click the New agent button in the top-right corner.
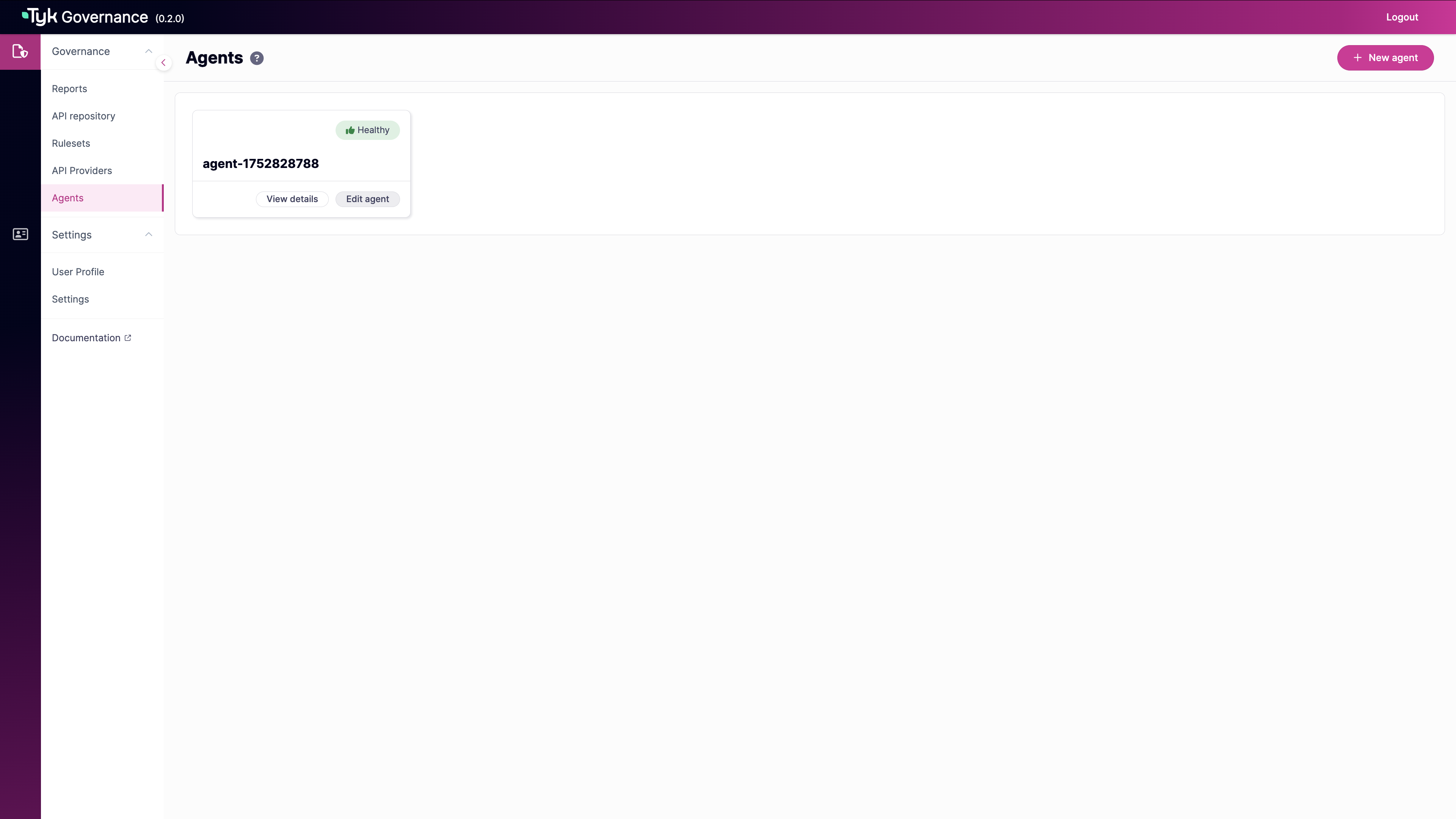
-
In the New agent form, enter:
- Name: A descriptive name for the agent (required)
- Description: Details about the agent’s purpose or location (required)
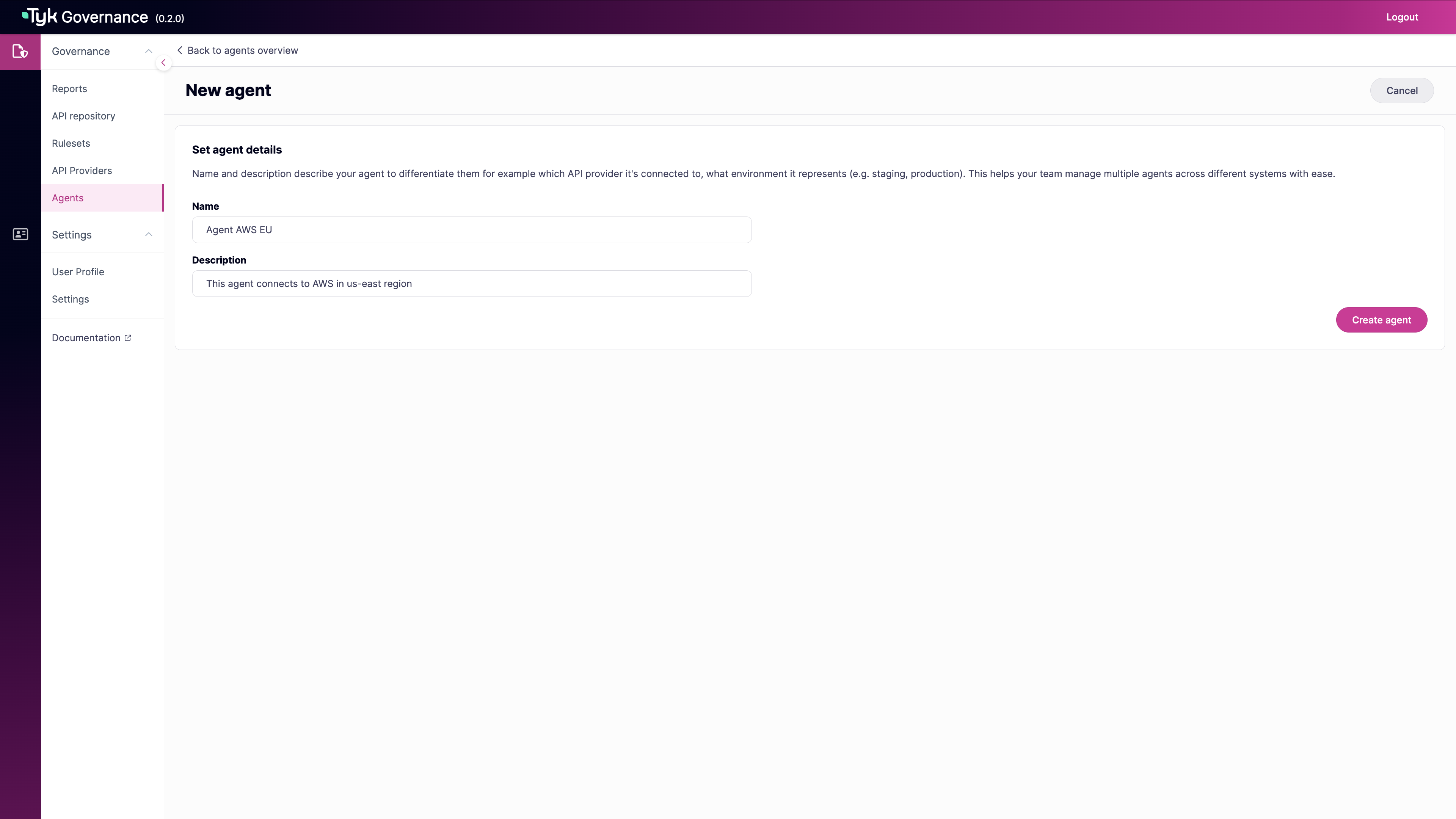
-
Click Create agent to save the new agent.
-
Alternatively, use the API to create a new agent:
Note the agent ID returned in the response:
-
From the Agents page, click the New agent button in the top-right corner.
-
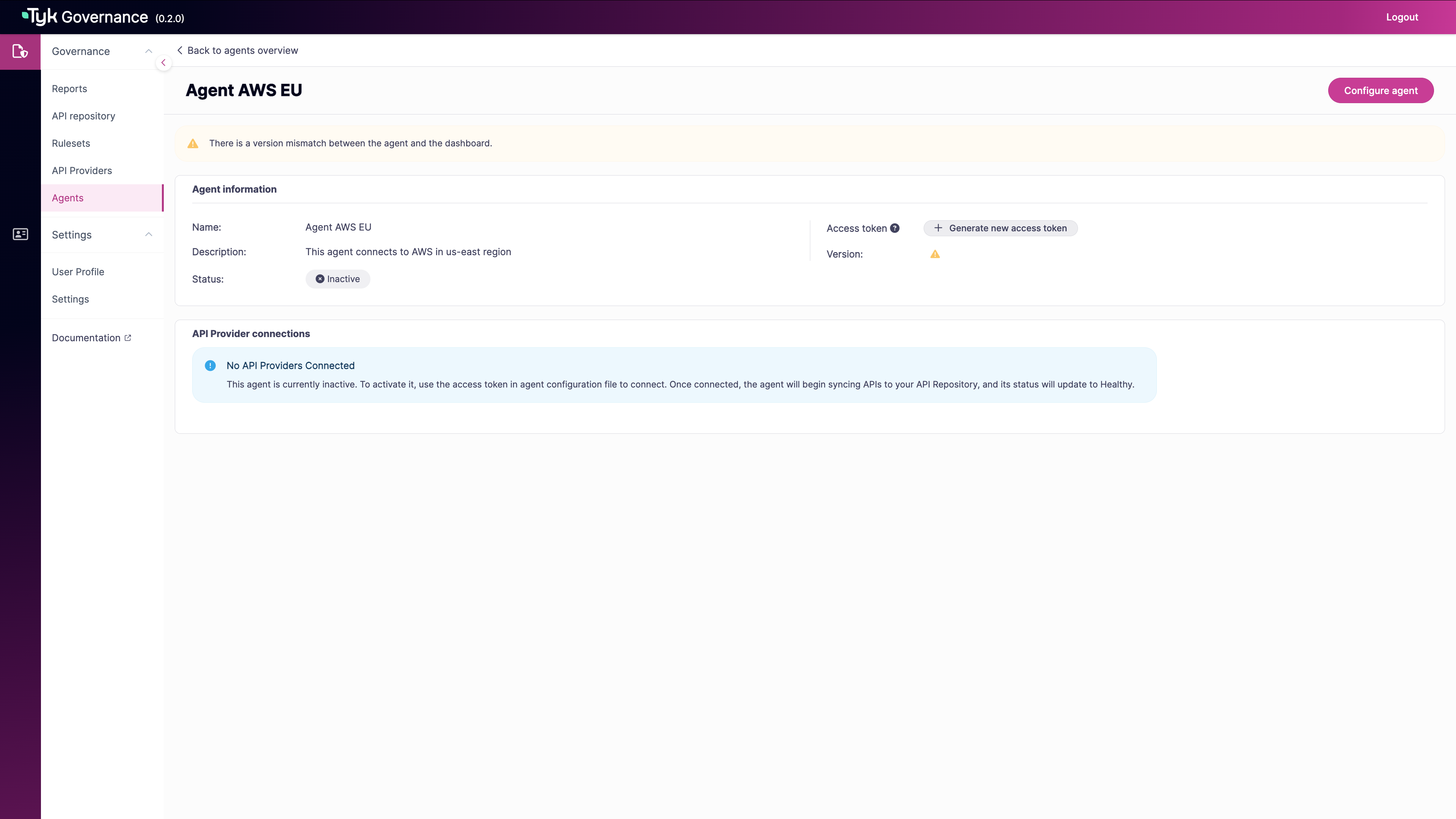
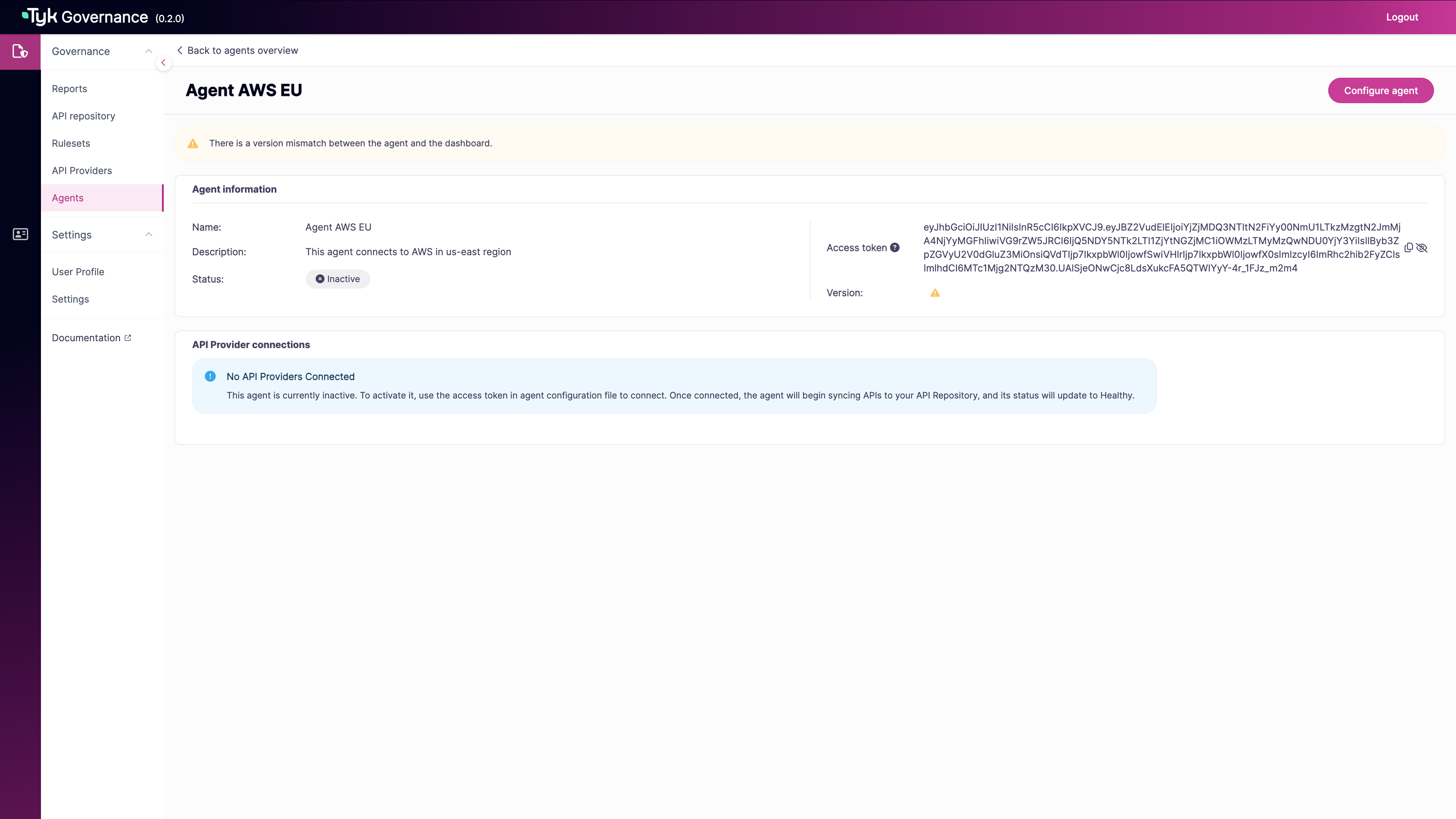
Generate an Agent Token
- In the Agent information section, find the Access token field.
- If no token exists, click Generate new access token.
-
For existing tokens:
- Click the eye icon to show/hide the token
- Use the copy icon to copy the token to your clipboard
- Use this token in your agent configuration file
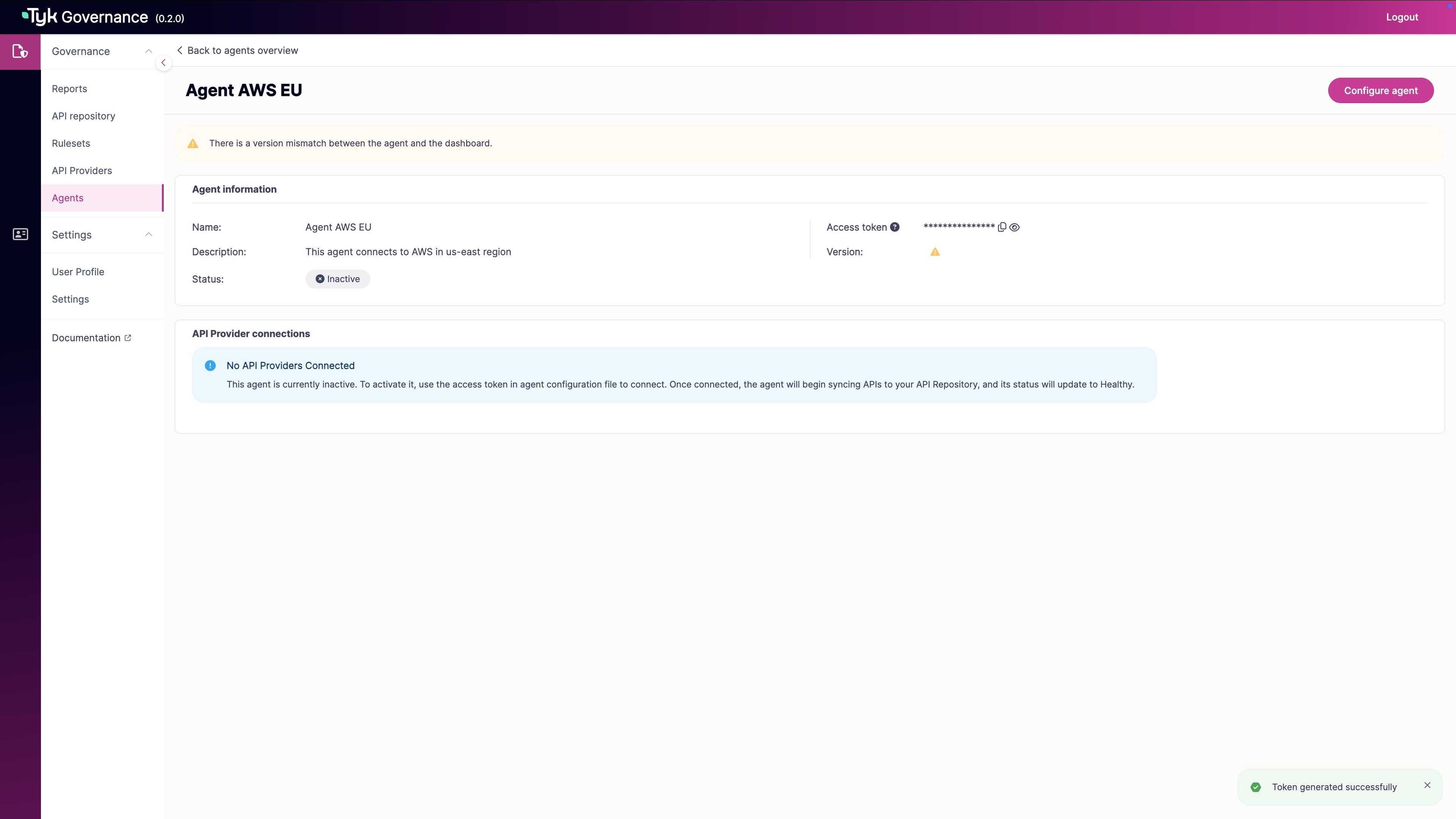
-
Alternatively, generate an authentication token for the agent using the API:
Save the token from the response:
-
Create Agent Configuration File
Create a file named
agent-config.yamlwith the following content: - Deploy the Agent Run the agent using Docker or as a Kubernetes Deployment. See Installation for details.
-
Monitor Agent Status
-
Check the agent status in the Governance Hub. A healthy agent will appear as “Healthy”:
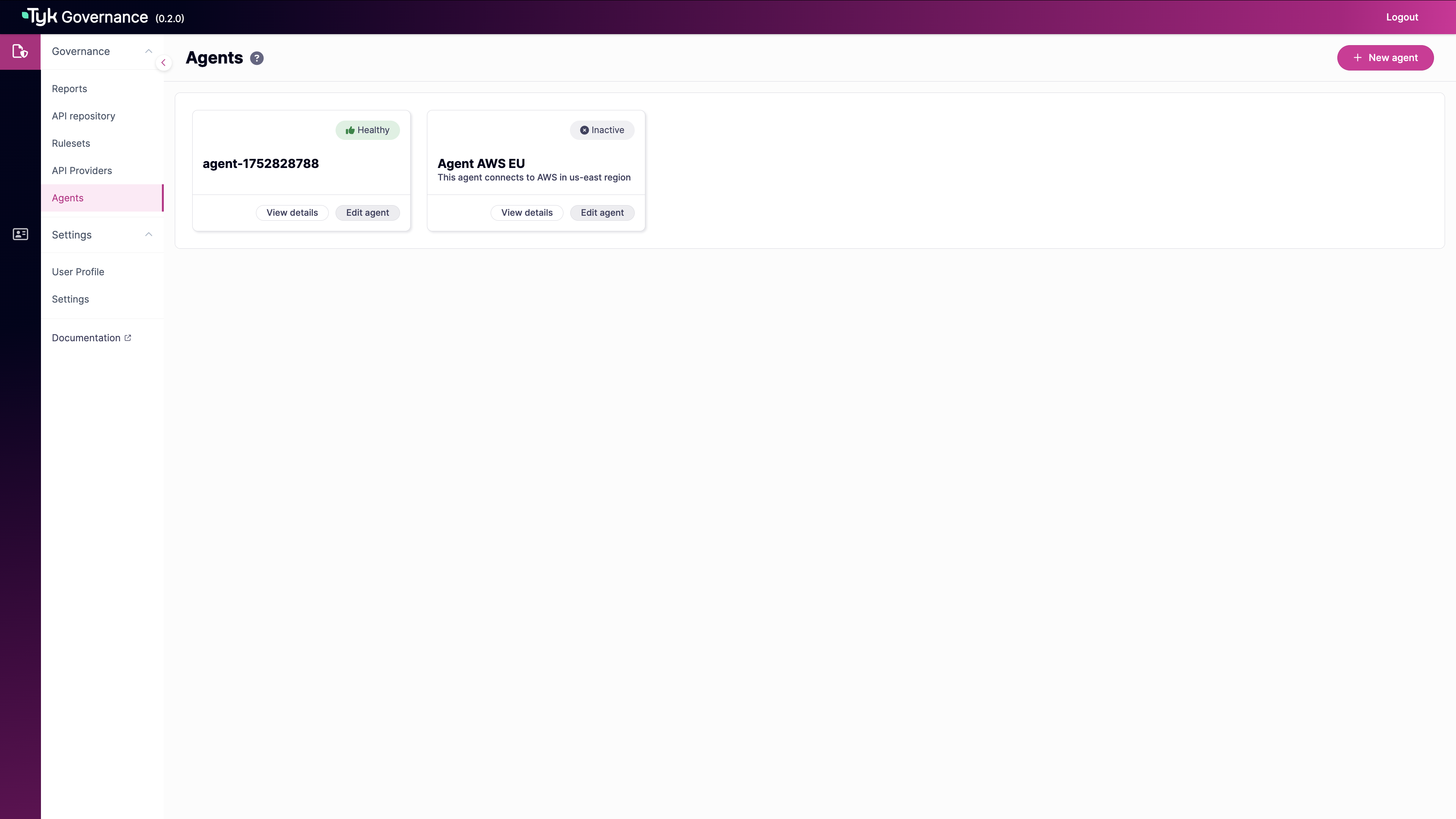
-
Check the agent status in the Governance Hub using API:
A healthy agent will show:
-
Check the agent status in the Governance Hub. A healthy agent will appear as “Healthy”:
- Trigger Initial Synchronization Trigger a synchronization to verify the agent is working correctly.
Validation
- The agent should appear as “Healthy” or have status as “ACTIVE” in the agent list
- The agent’s last heartbeat timestamp should be recent
- After synchronization, APIs from your providers should appear in the API Repository
How It Works
Agent Management works through a distributed architecture where agents deployed in your environments connect to the central Governance Hub using secure gRPC streams.Agent Architecture
The agent establishes two persistent gRPC streams with the Governance Hub:- Health Stream: Sends regular heartbeats to indicate the agent is alive and functioning
- Sync Stream: Used for API synchronization operations
Synchronization Process
Synchronization can be triggered in three ways:-
Manual Trigger: Through the Governance Hub UI or API
- Scheduled Sync: At regular intervals configured in the agent. See Understanding Scheduled Synchronization.
- Initial Connection: When an agent first connects to the Governance Hub
Understanding Scheduled Synchronization
You can configure scheduled synchronization for each API provider using the Governance Hub API (Hub-side scheduling). Use the/api/agents/{id}/sync-jobs endpoint to configure provider-specific schedules:
- The Governance Hub’s scheduler component manages the schedule
- The Hub initiates synchronization by sending requests to the agent
- It’s a “push” model where the Hub tells the agent when to sync
- You can set different schedules for different providers
- Supports Go duration format (e.g., “1h”, “12h”, “7d”)
- The agent receives a sync request from the hub (or initiates it based on its schedule)
- The agent queries each configured API provider for APIs
- The agent processes and normalizes the API definitions
- The agent streams the API definitions to the hub
- The hub processes and stores the API definitions
- The hub reconciles the API inventory, marking missing APIs as deleted
Deployment Scenarios
Multi-Provider API Discovery
Deploy agents to connect to different API providers across your organization, creating a comprehensive API inventory that spans platforms.High Availability Agent Deployment
Deploy multiple agent replicas in Kubernetes to ensure continuous API discovery even if some instances fail.Configuration Options
Agent Configuration File
The agent is configured using a YAML configuration file with the following sections:Core Configuration
API Provider Configuration
gRPC Connection (New in v0.2)
High Availability Configuration (New in v0.2)
Environment Variables
The agent supports configuration through environment variables:| Environment Variable | Description | Default Value |
|---|---|---|
TYK_AGENT_LICENSEKEY | Your Tyk Governance license key | - |
TYK_AGENT_LOGLEVEL | Log level (debug, info, warn, error) | info |
TYK_AGENT_GOVERNANCEDASHBOARD_SERVER_URL | The gRPC endpoint URL of the Tyk Governance service | - |
TYK_AGENT_GOVERNANCEDASHBOARD_SERVER_TLS_ENABLED | Enable TLS for gRPC connections | false |
TYK_AGENT_GOVERNANCEDASHBOARD_SERVER_TLS_CACERTPATH | Path to CA certificate | - |
TYK_AGENT_GOVERNANCEDASHBOARD_SERVER_TLS_CLIENTCERTPATH | Path to client certificate (for mTLS) | - |
TYK_AGENT_GOVERNANCEDASHBOARD_SERVER_TLS_CLIENTKEYPATH | Path to client key (for mTLS) | - |
TYK_AGENT_GOVERNANCEDASHBOARD_SERVER_TLS_INSECURESKIPVERIFY | Skip verification of server certificate | false |
TYK_AGENT_GOVERNANCEDASHBOARD_AUTH_TOKEN | Authentication token for the agent | - |
TYK_AGENT_HEALTHPROBE_SERVER_PORT | Port for health probe server | 5959 |
gRPC Connection Variables (New in v0.2)
| Environment Variable | Description | Default Value |
|---|---|---|
TYK_AGENT_RPC_KEEPALIVE_ENABLED | Enables/disables keepalive | true |
TYK_AGENT_RPC_KEEPALIVE_TIME | Duration after which ping is sent | 30s |
TYK_AGENT_RPC_KEEPALIVE_TIMEOUT | Duration client waits for ping response from the server | 20s |
TYK_AGENT_RPC_KEEPALIVE_PERMITWITHOUTSTREAM | Allows sending pings without active streams | true |
Leader Election Variables (New in v0.2)
| Environment Variable | Description | Default Value |
|---|---|---|
TYK_AGENT_LEADERELECTION_ENABLED | Enable Kubernetes leader election | false |
TYK_AGENT_LEADERELECTION_LEASENAME | Name of the lease object | governance-agent-lock |
TYK_AGENT_LEADERELECTION_LEASENAMESPACE | Namespace for the lease object | Agent’s namespace |
TYK_AGENT_LEADERELECTION_LEASEDURATION | Duration for lease | 15s |
TYK_AGENT_LEADERELECTION_RENEWDEADLINE | Deadline for renewing leadership | 10s |
TYK_AGENT_LEADERELECTION_RETRYPERIOD | Period between retry attempts | 2s |
Required Environment Variables for Leader Election
When leader election is enabled, the following environment variables must also be set:POD_NAME: The name of the pod (used as the identity for leader election)POD_NAMESPACE: The namespace of the pod (used for creating the lease object)
Use Cases
Multi-Region API Discovery
For organizations with APIs deployed across multiple geographic regions, deploy region-specific agents to efficiently discover and monitor APIs while respecting network boundaries. Implementation:- Deploy agents in each region where APIs are hosted
- Configure each agent with the appropriate regional API providers
- Use descriptive names to identify regional agents
- Monitor all agents from the central Governance Hub
- Reduced latency for API discovery operations
- Respect for network boundaries and security zones
- Improved reliability with region-specific agents
- Clear organization of APIs by region
Secure Environment Bridging
For organizations with strict network segmentation, use agents to securely bridge between isolated environments without compromising security boundaries. Implementation:- Deploy agents in each network segment
- Configure outbound-only connections from agents to the Governance Hub
- Use separate agents for production and non-production environments
- Implement appropriate network security controls around agent traffic
- Maintain network isolation while enabling governance
- No inbound connections required to sensitive environments
- Granular control over which APIs are discovered
- Separation of concerns between environments
Automated API Lifecycle Tracking
Use scheduled synchronization to automatically track the lifecycle of APIs, including when they’re created, updated, or deleted from source providers. Implementation:- Configure agents with scheduled synchronization
- Set appropriate sync intervals based on change frequency
- Use the API Repository to monitor API status
- Create reports showing API lifecycle events
- Automatic detection of API changes
- Historical record of API lifecycle events
- Reduced manual tracking effort
- Improved visibility into API landscape evolution
Best Practices and Recommendations
- Use descriptive agent names that indicate their purpose and scope
- Deploy agents close to API providers to minimize latency and network issues
- Configure appropriate sync intervals based on how frequently your APIs change
- Use leader election for high availability when deploying multiple agent replicas
- Monitor agent health regularly to ensure continuous API discovery
- Rotate API provider credentials periodically for better security
- Use the principle of least privilege when configuring API provider credentials
- Start with manual syncs before enabling scheduled synchronization
- Implement network security controls around agent traffic
- Maintain agent versions to ensure compatibility with the Governance Hub
FAQs
How many agents do I need?
How many agents do I need?
The number of agents depends on your API landscape. Generally, you should consider deploying separate agents for:
- Different network segments or security zones
- Different geographic regions
- Different environments (production vs. non-production)
- Different API provider types with many APIs
What happens if an agent goes offline?
What happens if an agent goes offline?
If an agent goes offline, it will be marked as “INACTIVE” in the Governance Hub after missing several heartbeats. APIs discovered by that agent will remain in the repository but won’t be updated until the agent reconnects or another agent is configured to find out the same APIs.When using high availability with leader election, if the leader agent goes offline, another replica will automatically take over the leadership role and continue synchronization operations.
How secure is the agent-to-hub communication?
How secure is the agent-to-hub communication?
All communication between agents and the Governance Hub is secured using:
- TLS encryption for all traffic
- JWT token-based authentication
- Regular token validation
- Bidirectional stream validation
What permissions do agents need for API providers?
What permissions do agents need for API providers?
Agents require read-only access to API configurations:
- For Tyk Dashboard: An API key with read access to APIs and policies
- For AWS API Gateway: IAM credentials with permissions to list and get API Gateway resources
- For other providers: Similar read-only access to API configurations
Troubleshooting
Agent shows as "INACTIVE"
Agent shows as "INACTIVE"
- Check if the agent process is running
- Verify network connectivity to the Governance Hub
- Ensure the agent token is valid and not expired
- Check agent logs for connection errors
- Verify the Governance Hub URL is correct
- Ensure the agent has outbound access to the hub’s gRPC port. It is usually 50051 for self-managed instances. For Tyk Cloud managed instance, it is proxied through port 443.
Agent connects but no APIs are discovered
Agent connects but no APIs are discovered
- Verify API provider credentials are correct
- Check agent logs for provider connection errors
- Ensure the provider has APIs configured
- Try triggering a manual sync operation
- Check agent configuration for correct provider URLs
- Verify the agent has network access to the API providers
Multiple agents running when using leader election
Multiple agents running when using leader election
- Verify leader election is properly configured
- Check if agents are in the same Kubernetes namespace
- Ensure agents are using the same lock name
- Check Kubernetes permissions for leader election
- Verify Kubernetes API access from agent pods
- Check agent logs for leader election messages
Scheduled sync not working
Scheduled sync not working
- Ensure the agent has been running long enough for a scheduled sync
- Check agent logs for scheduled sync messages
- Try restarting the agent to reset the schedule
- Verify the agent is the leader if using leader election